OWASP ZAP (Zed Attack Proxy) is an open source penetration testing application developed by large society of volunteers linked with Open Web Application Security Project organisation.
ZAP is a cybersecurity testing tool capable of performing a wide range of attacks against any web application. It is designed for various level of skills, from trainee web developers to cybersecurity professionals. It act as an attacker's proxy, similarly to man in the middle attack.
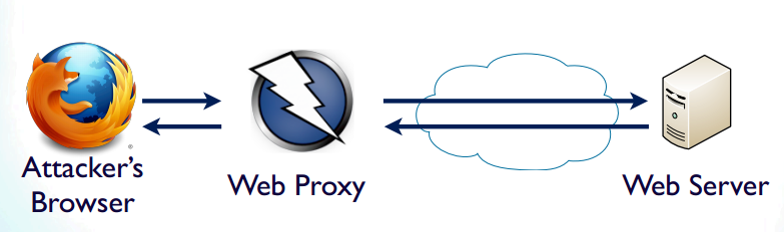 This software is capable of performing various web service attacks such as hidden services scanning, checks against known vulnerabilities, brute-force password cracking, intercepting data and much more. With vast library of mods delivered by whole society ZAP is able to launch an attack against very specific aspect of certain type web app, and the most recently recognized exploits. It can also act as a browser plug-in, providing attacker with normally hidden information, for example HTTP headers and contents of cookies.
This software is capable of performing various web service attacks such as hidden services scanning, checks against known vulnerabilities, brute-force password cracking, intercepting data and much more. With vast library of mods delivered by whole society ZAP is able to launch an attack against very specific aspect of certain type web app, and the most recently recognized exploits. It can also act as a browser plug-in, providing attacker with normally hidden information, for example HTTP headers and contents of cookies.While this is extremely useful webdev tool, common sense needs to be applied - this is a software performing real attacks on freely specified target. Experimenting with live web services might be seen as a cyber crime.

Comments
Post a Comment